The CSPM dashboard acts as a central command center, consolidating critical information from various cloud platforms and presenting it in a user-friendly manner. It serves as a single source of truth for security administrators, enabling them to monitor, assess, and remediate security risks across their cloud infrastructure. This chapter aims to equip you with a solid understanding of how the dashboard functions, its key features, and its role in enhancing cloud security. You will gain insights into the primary objectives of the dashboard and how it facilitates comprehensive security management, the core features and components of the CSPM tool, customization and configuration possibilities, data visualization, and reporting. You will also explore different dashboards, such as the compliance dashboard, identity dashboard, vulnerability dashboard, and reporting dashboard.
By the end of this chapter, you will have gained a comprehensive understanding of the purpose of CSPM dashboards, their key features, and their role in bolstering cloud security.
We’ll be covering the following main topics:
- General dashboard overview
- Custom dashboards
- Exporting dashboards
- Best practices for effectively using CSPM dashboards
Let’s get started!
Reviewing general dashboard types
The CSPM dashboard is a centralized user interface that provides a comprehensive view of an organization’s cloud security posture and allows security administrators to monitor and manage security risks across their cloud environments. The primary purpose of the CSPM dashboard is to enhance cloud security management by offering real-time visibility into potential vulnerabilities, misconfigurations, and compliance gaps within the cloud infrastructure. It serves as a command center for security teams, enabling them to assess risks, enforce security policies, and take proactive measures to protect sensitive data. The specific design and layout of a CSPM dashboard vary depending on the provider or tool being used. A wide range of dashboards will be discussed in this chapter in the form of use cases. It is not necessary to find all these dashboards under one tool. Some of them are more common, while some can be created using the dashboard customization feature provided by vendors. The following screenshot provides a glimpse of what the dashboard of a CSPM tool looks like. Typically, it includes the overall secure score, risk summary, and recommendations:
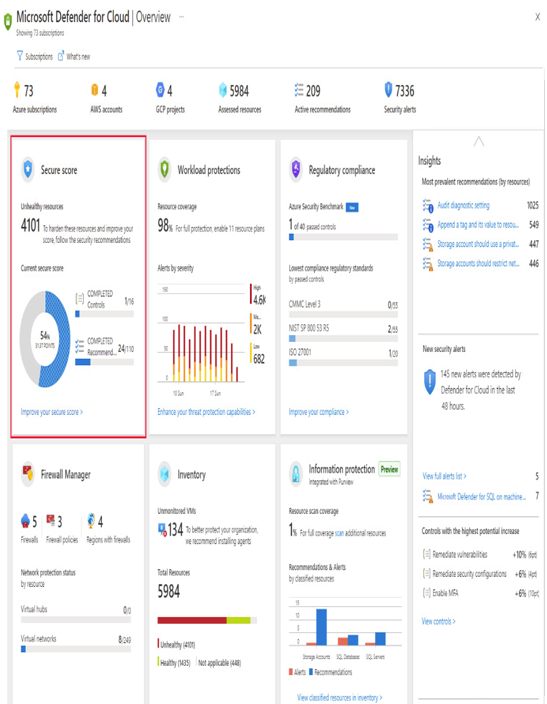
Figure 10.1 – Microsoft Defender for Cloud dashboard overview (source: https://learn.microsoft.com/en-us/azure/defender-for-cloud/overview-page)
Note
The figures in this chapter provide a visual understanding of various dashboard types based on their availability.
The type of CSPM dashboard you choose can depend on factors such as the cloud service providers you use, the complexity of your cloud environment, and your organization’s security needs. Let’s look at some common types of CSPM dashboards.
