The identity dashboard of a CSPM tool is a component that’s designed to provide insights and oversight into the Identity and Access Management (IAM) aspects of an organization’s cloud environment. It focuses on managing user identities, access permissions, authentication, and authorization within cloud services. The goal of an identity dashboard is to enhance security by ensuring that only authorized users have appropriate access to cloud resources. The following screenshot depicts the identity risk dashboard of the Orca CSPM tool:
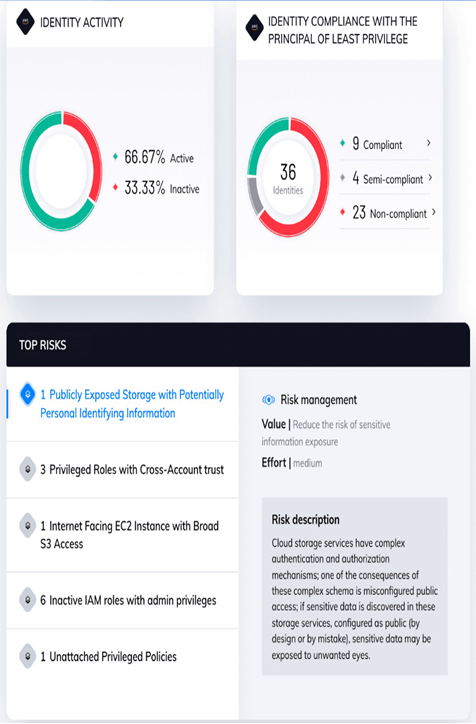
Figure 10.5 – Orca CSPM identity risk dashboard (source: https://orca.security/resources/blog/ciem-cloud-identity-entitlements-management-beyond-identity-hygiene-risks/)
Note
Many security companies offer identity-specific services under separate product lines such as Cloud Infrastructure Entitlement Management (CIEM), which allows you to track your cloud platforms’ users, roles, groups, and policies in one place. In the most recent trend, due to competition and other reasons, it is observed that various features are combined into one product and hence some CSPM vendors have already started offering CIEM features under their CSPM products.
Here is an explanation of the key features and functionalities of an identity dashboard:
- User and group management: The identity dashboard displays a list of all users and groups that have access to the cloud environment. It allows administrators to view, add, modify, or remove user accounts and groups.
- Access permissions: For each user or group, the dashboard shows their assigned roles, permissions, and access levels across various cloud resources. This helps administrators ensure that permissions are aligned with the principle of least privilege.
- Role-based access control (RBAC): The dashboard highlights the roles defined within the cloud environment and shows which users or groups are associated with each role. It ensures that users have appropriate access based on their roles and responsibilities.
- Authentication methods: The dashboard provides an overview of the authentication methods being used, such as passwords, multi-factor authentication (MFA), or single sign-on (SSO). It allows administrators to monitor and enforce strong authentication practices.
- Access policies: Organizations often define access policies to control user access to resources. The identity dashboard may display these policies and their associated users, helping administrators verify that access is compliant with policies.
- Privileged users: The dashboard may/should highlight privileged users with elevated access levels and showcase their activities and permissions. This is crucial for ensuring oversight and accountability.
- Access reviews: An identity dashboard may include a feature for conducting access reviews. This involves periodically assessing and verifying that users’ access permissions are still necessary and appropriate.
- User activity monitoring: Some dashboards include logs of user activities, showing what actions users have performed and which resources they accessed. This information aids in detecting unauthorized or suspicious activities.
- Integration with identity providers: If an organization uses external identity providers for authentication and SSO, the dashboard might display integrations and configurations related to these providers.
- Compliance auditing: The dashboard includes features to assist with compliance audits. It helps administrators demonstrate that access controls are managed effectively and align with regulatory requirements.
- User onboarding and offboarding: The dashboard may streamline the process of adding or removing users by providing templates for common roles and permissions during onboarding and offboarding procedures.
- API access management: For cloud services that offer APIs, the identity dashboard displays information about API keys, tokens, and their associated permissions.
- Access anomaly detection: Advanced IAM dashboards may employ machine learning algorithms to detect anomalous access patterns, such as unusual login locations or unauthorized role changes. This helps with identifying potential security incidents.
In summary, an identity dashboard within a CSPM tool focuses on managing and monitoring user identities and their access to cloud resources. By providing visibility into identity-related aspects and ensuring that access permissions are correctly configured and regularly reviewed, the dashboard contributes to maintaining a secure and well-governed cloud environment. Now, let’s look at network security dashboards.
